****
Our Innovation.
A Dynamic Partial Identity Architecture
Dynamic Partial Identity (DPID), patented identity framework, introduces a new architectural model for identity security — designed to prevent credential reuse, replay attacks, and large-scale identity compromise.
By replacing static identifiers with time-bound, context-specific identity fragments, DPID fundamentally reduces the usefulness of stolen identity data and limits the blast radius of breaches across digital and physical identity systems.
Revolutionising Identity Protection
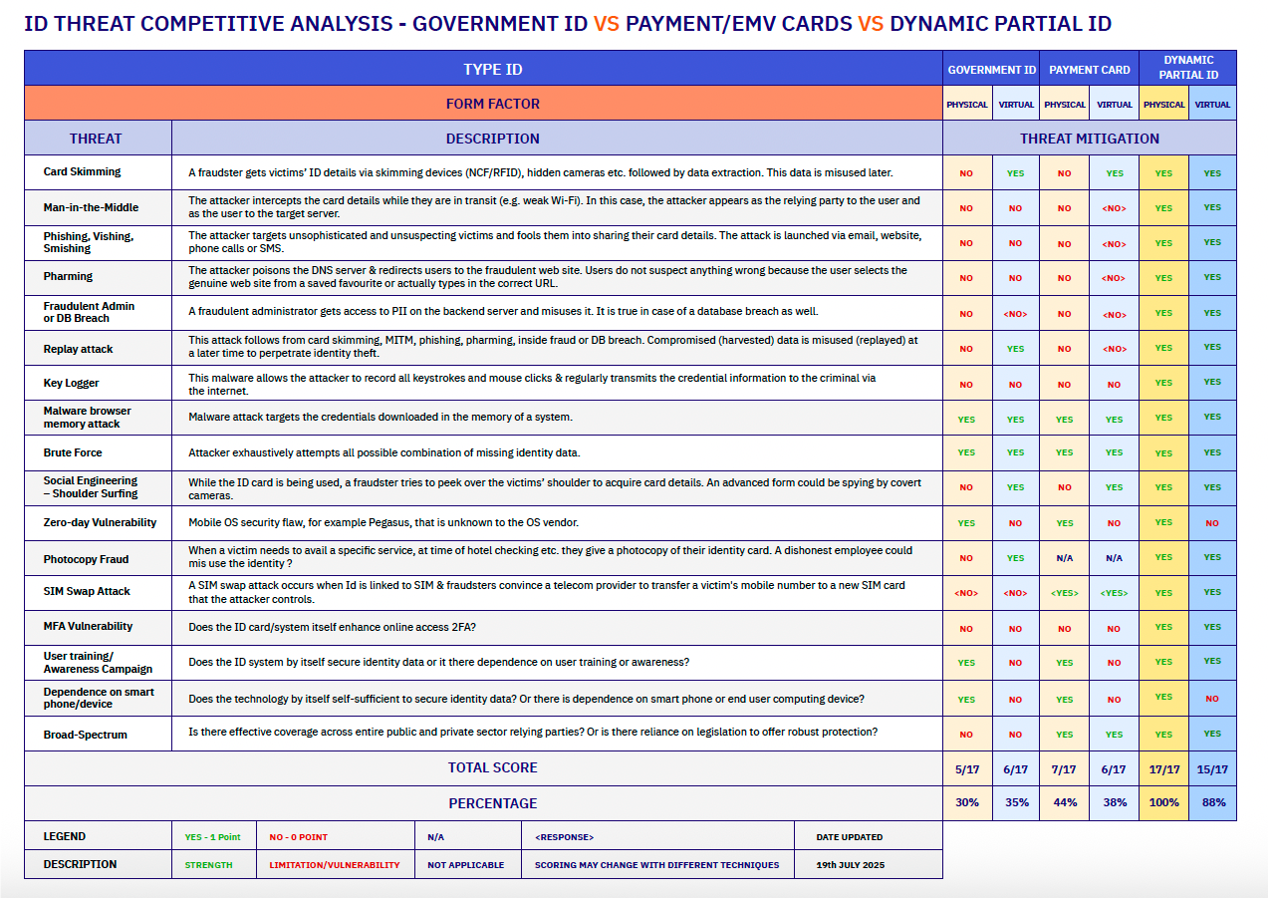
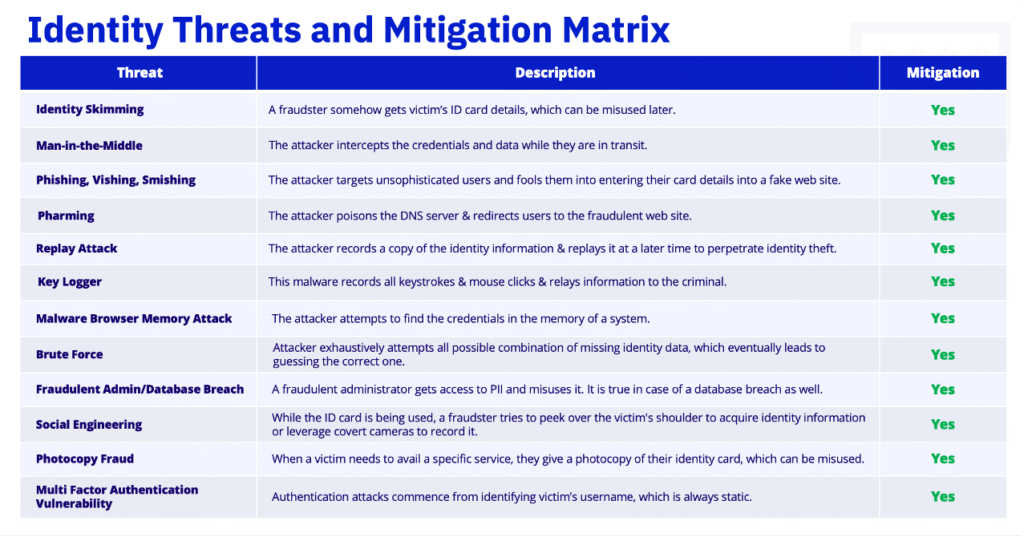
Identity fraud costs individuals, businesses, and governments over one trillion dollars globally each year, affecting nearly every form of digital and physical identity in use today.
The root cause is structural: modern identity systems rely on static identifiers that, once exposed, can be reused, replayed, and exploited at scale.
Dynamic Partial Identity (DPID) introduces a new architectural approach. Instead of exposing complete, reusable identifiers, DPID enables systems to use time-bound, context-specific identity fragments, while complete identities are reconstructed only by authorised systems under controlled policy.
By design, this limits the usefulness of stolen identity data and reduces the impact of breaches across online services, payment ecosystems, and government-issued credentials.
The same principle applies consistently across identity environments — including government credentials, financial instruments, enterprise access, and digital accounts — without requiring users to adopt complex new behaviours.
Rather than displaying or transmitting complete identifiers, systems can rely on renewable, partial identity values, significantly reducing the risks associated with interception, reuse, and large-scale compromise.

The card displays only partial, time-bound identity values while complete identities remain protected within authorised systems.
ZIEL™ Research (Zero Identifier Exposure Layer)
ZIEL™ Research is our research-driven identity architecture initiative focused on addressing fundamental and structural weaknesses in modern identity systems.
It explores identity protection models for environments where static credentials are no longer defensible, and defines the architectural principles of the Zero Identifier Exposure Layer, which underpin next-generation identity protection architectures, including Dynamic Partial Identity (DPID).
This research informs a patented core identity architecture that underpins Dynamic Partial Identity (DPID) and its operational frameworks.
From Research to Architecture: PIAL™
Building on the principles defined by the Zero Identifier Exposure Layer, PIAL™ (Programmable Identifier Assurance Level) provides the operational framework that governs how identity is issued, bound to context, and validated in real-world systems.
PIAL™ enables identity systems to apply graduated assurance levels dynamically based on risk, regulatory requirements, and relying-party trust posture. These levels can determine how identity fragments are generated, how long they remain valid, and the conditions under which they can be accepted.
By controlling identity validity, context binding, and exposure limits, PIAL™ ensures that identity use remains proportionate to the assurance level required, reducing the risk of reuse, replay, and misuse.